Networked building management systems bring many benefits but can expose organisations to cyber security breaches. This module, sponsored by Schneider Electric, examines the key ways to guard against attack

How to take this module
UBM’s CPD distance-learning programme is open to anyone seeking to develop their knowledge and skills. Each module also offers members of professional institutions an opportunity to earn between 30 and 90 minutes of credits towards their annual CPD requirement.
This article is accredited by the CPD Certification Service. To earn CPD credits, read the article and then click the link below to complete your details and answer the questions. You will receive your results instantly, and if all the questions are correctly answered, you will be able to download your CPD certificate straight away.
CPD CREDITS: 60 MINUTES
DEADLINE: 18 AUGUST 2015

Cybersecurity attacks are becoming increasingly common and pose a global threat – no region or company is immune. Data breaches and cyber crime cost companies billions each year, and the damage to brand reputation can be even more costly. �ڶ����� management systems (BMSs), once separate, are now firmly integrated with companies’ IT infrastructure. Today’s intelligent building management systems are networked with data centres, remote access servers and utilities through open protocols. While these intelligent systems provide significant benefits, they also expose companies to greater cybersecurity risks. This CPD will look at best practice for protecting them from attack.
INTRODUCTION TO IP CONVERGENCE
A range of factors is driving greater building automation and integration between building systems, including rising energy costs and government regulation on energy efficiency, higher expectations of comfort and security within buildings, and demand for more granular, real-time information about how they are running. In order to maximise efficiency, a growing number and range of systems are monitored and controlled automatically, and there is an increasing focus on interaction between them.
The majority of building systems are now IT-enabled and can be interconnected over an IP network. IP stands for “internet protocol”, the most widely used set of rules for exchanging data across networks. In an IP network, each device is given a unique IP address and this is used to route data around the system. More and more systems and devices are able to be linked in this way, a trend known as IP convergence, which extends far beyond building control systems. There is also an increase in open standards and proprietary commercial products to make integration easier.
A single IP network can carry:
- �ڶ����� systems For example, building management, HVAC, climate control and monitoring, energy metering/billing, power supply, lift control, lighting control
- Security systems For example, access control/ID systems, video surveillance/analytics, intrusion detection, fire and life safety, gateway to first responders
- Business systems For example, voice and data communications, video conferencing, enterprise business applications and IT services, financial systems, booking systems.
The benefits of IP convergence in the built environment include:
- Reduced capital expenditure Software and installation costs are lower, as all systems use common cabling and wireless infrastructure. Using Power over Ethernet (PoE), where both electrical power and data connectivity are delivered to a device through the same ethernet cable, can also eliminate the need for separate cabling systems while offering greater control and flexibility. IP networks are flexible and adaptive, so as technology evolves companies can add features to their existing networks without the need for additional infrastructure.
- Lower operating costs �ڶ����� automation means fewer staff are required, and having just one system reduces the time and cost of training. Maintenance costs can be minimised with a single service contract, and bills are lower, as intelligent systems optimise energy use.
- Simplicity As there is a single system, a standard process can be used, with relevant information generated for each job role rather than for each product or system and available remotely from any location.

CYBER SECURITY RISKS TO BUILDING SYSTEMS
The threat of a cyber attack is a real one, and may come from many sources, within or outside the organisation – a disgruntled employee, organised crime, terrorists or competitors. It may also be unintentional, caused by error, omission, ignorance or negligence by staff, contractors or suppliers. An attack can cause disruption to building, security and business systems and a loss of control or visibility, which can lead to significant safety, operational and reputational risks.
There are already many examples of how building systems may be compromised. In November 2013, hackers gained access to payment card details for 40 million customers of US retailer Target by using authentication credentials stolen from its HVAC subcontractor. Speaking at a hacking conference in Las Vegas last year, security consultant Jesus Molina revealed how he had been able to take control of lighting, blinds and temperature systems in 200 luxury hotel rooms in Shenzen, China, using the iPad in his room. Meanwhile, the Stuxnet virus reportedly ruined one-fifth of Iran’s nuclear centrifuges by attacking the computers used to automatically control them.
These risks are increasing constantly as more and more building elements come to be linked into the internet. Ubiquitous connectivity through GPS, smartphones and the “Internet of Things”, where IP-linked systems speak to each other without the need for human control, all pose challenges in security and privacy. Today’s smart homes are connected to the internet through televisions, webcams, remote power outlets, and access control and lighting systems.
Vulnerability can also extend outside intelligent buildings themselves. There is now much discussion of “smart cities”, where digital systems are used to run public services such as energy distribution or transport and mobility, resulting in new security vulnerabilities – if traffic and transit management or congestion charging systems are threatened, a city could quickly become gridlocked.
By way of example, a computer virus could cripple a country’s national infrastructure through the following process:
- A virus is placed on to a USB drive which is plugged into a computer on a secure network.
- The virus scans through the network and the updated virus targets specific computers.
- The virus subverts computers running specific programs or components and sends back false messages that the plant/systems are fine.
- The virus now controls the plant or machines and damages equipment, compromising the building.
- The virus spreads to other interconnected systems and infrastructure, potentially causing a national infrastructure collapse.
This may sound extreme but consider the following question: if you saw a USB stick lying around, what would you do?
CYBER SECURITY
Cyber security addresses attacks on computer systems and networks that can cause accidental or intentional disruptions. It is now widely recognised as a body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorised access. Cyber security is important to minimise business interruption and production downtime, maximise operational integrity and safety, and protect intellectual property. It also enables companies to demonstrate internal governance and comply with international standards.
Cyber security requirements need to be identified throughout all stages of the life cycle of an intelligent BMS, as follows.
PASSWORD MANAGEMENT
Properly managing users and passwords is critical to securing any building management system – most attacks are successful because a password has been compromised. The importance of changing default passwords for every installation should not be underestimated: this should be the first action on initialising a new device. Products are usually shipped from the manufacturer with minimal security credentials to allow for easy system setup. However, the longer that a device sits with default credentials, the greater the likelihood that it could be compromised.
Simple alphabetic passwords do not provide sufficient security, because hackers can use machines that test billions of passwords a second. To provide any level of real protection, only complex passwords with more than 10 characters should be used.
Information about devices is valuable to any hacker. Once they are armed with sensitive network information, it is a relatively simple process to access a device and identify credentials. The device’s information can then be harvested and either stored or sold. This process happens continually and means that no internet-connected devices are safe.
The table below identifies vulnerabilities associated with passwords and recommended best practices.
| Vulnerability | Reason | Best practice |
|---|---|---|
| Default credentials | Available in online databases | Change default passwords immediately |
| Simple passwords | Easily cracked | 10 to 15-character multi-type passwords |
| Demonstration systems | Hard-coded credentials | Change defaults before connecting to the internet |
| Same credentials for all sites | All sites at risk if credentials hacked | Unique credentials for each site |
| Credentials shared among a group of users | Lack of traceability and accountability | Require unique credentials per user |
| Source: Five Best Practices to Improve �ڶ����� Management Systems (BMS) Cybersecurity, Gregory Strass & Jon Williamson, Schneider Electric | ||

SECURE DESIGN
During the design phase of a building, the cyber security and resilience requirements of the building and its systems and devices should be established and the primary focus should be on providing means to control and monitor access. This includes:
- Physical security Control access to the building, room, cabinet, routers, firewalls and switches and prevent unauthorised access to devices, networks and information. For example, critical devices would be located in a locked cabinet or protected using access controls, and communication cable runs might be protected with conduits or ruggedised conduits.
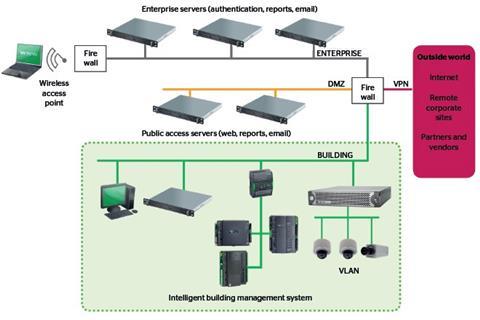
- Network infrastructure Limit network access points and secure all points of access. Create logical boundaries. Use firewalls to control the flow of information. They can determine which traffic is allowed to pass through onto the network, and should be used at each transition point into and out of the building management system network. Figure 1 (opposite) illustrates how firewalls can be used to isolate the building from the enterprise servers, public access servers and outside world via the internet.
- Manage user access Restrict user access by using central user authorisation packages, such as Microsoft’s Active Directory or smartcards. Restrict remote access and use secure connections (for example, a virtual private network, or VPN) and secure protocols (such as HTTPS or SSH). Create a “demilitarised zone” (DMZ) or perimeter network to add an extra layer of security and enable safe public access to certain information. This contains the outward-facing aspects in a separate part of the system.
SECURE INSTALLATION
This involves maintaining physical security and implementing system security, as well as managing the supply chain – during the installation phase, the BMS could be vulnerable to attack due to a steady turnover of personnel among contractors and subcontractors. Monitoring the design integrity is also critical as new devices and software are introduced.
- Harden system devices Remove removable media (for example, USB memory sticks, compact discs). Enable security features in each device (for example, secure ports, encryption, access control, user authorisation). Check devices’ web interface security with manufacturer. If internet access is required, insert firewall between the device and the internet. Install antivirus or security management packages from a reputable vendor.
- Enable threat detection and mitigation Create logs to monitor network and device activity, physical access, user activity and so on, and use penetration-testing software. Measures should be in place to ensure logging does not affect the load and performance of the system.
- Configure user accounts Replace default passwords with complex passwords. Remove any permissions a user does not need to perform their job. Set account policies to use expiration dates and force password changes.
SECURE OPERATION
This includes monitoring the system and raising awareness of cyber security, and developing and maintaining cyber security processes. During the operational phase, security should be proactively managed to identify any additional requirements arising from changes in the building’s use.
- Monitor the system Use monitoring, analysis tools, incident reporting and inventory packages to generate alerts.
- Build security awareness Security policies and procedures are key, and it is important to conduct training and raise awareness about each person’s role and their responsibilities. Manage user accounts and access lists for new starters and leavers, changes of role and so on. Use trusted sources and stay up to date with vendor firmware updates, service packs and hot fixes, preferably using digital signatures. When attacking a device, hackers will typically first determine whether all security patches have been installed. When security systems are not up to date there are usually weak areas that can be exploited.
- Develop method statements for installation of hardware and software, backup and recovery procedures and a firewall management plan.
- Perform security audits An effective audit assists in the ongoing process of improvement. Organisations should provide a means to ensure that systems, policies and procedures are effective and that there are no gaps. Report past breaches, including attempts to acquire passwords, procedures not being followed and any new threats.
INFORMATION SECURITY MANAGEMENT METHODOLOGY
Cyber attacks happen all the time and there is no such thing as absolute security. As such, organisations must have an information security management methodology in place. The international standard ISO 27001 provides the requirements for an information security management system and recommends a “plan, do, check, act” process.
- “P������” includes carrying out a risk analysis to develop security measures and draw up procedures and policies
- ����” involves implementing these policies, carrying out training and raising awareness
- “C���” involves detecting incidents and monitoring compliance and effectiveness of security measures
- “A����” involves rectifying any issues and optimising security measures.
This cycle should be repeated regularly.

FURTHER READING
- Best Practices for Securing an Intelligent �ڶ����� Management System, Schneider Electric �ڶ�����s IT Security Group
- Resilience and Cyber Security of Technology in the Built Environment, Hugh Boyes, IET Standards Technical Briefing
- Five Best Practices to Improve �ڶ����� Management Systems (BMS) Cybersecurity, Gregory Strass & Jon Williamson, Schneider Electric
- Information Security: Preparing for the Next Hack Attack, Dr Boris Piwinger, AT Kearney
- How Can I… Reduce Vulnerability to Cyber Attacks, PlantStruxure Technical Note, Schneider Electric
- Intelligent �ڶ�����s: Understanding and Managing the Security Risks, IET Sector Insights

How to take this module
UBM’s CPD distance-learning programme is open to anyone seeking to develop their knowledge and skills. Each module also offers members of professional institutions an opportunity to earn between 30 and 90 minutes of credits towards their annual CPD requirement.
This article is accredited by the CPD Certification Service. To earn CPD credits, read the article and then click the link below to complete your details and answer the questions. You will receive your results instantly, and if all the questions are correctly answered, you will be able to download your CPD certificate straight away.
CPD CREDITS: 60 MINUTES
DEADLINE: 18 AUGUST 2015
Privacy policy
Information you supply to UBM Information Ltd may be used for publication and also to provide you with information about our products or services in the form of direct marketing by email, telephone, fax or post. Information may also be made available to third parties. UBM Information Ltd may send updates about �ڶ����� CPD and other relevant UBM products and services. By providing your email address you consent to being contacted by email by UBM Information Ltd or other third parties. If at any time you no longer wish to receive anything from UBM Information Ltd or to have your data made available to third parties, contact the Data Protection Coordinator, UBM Information Ltd, FREEPOST LON 15637, Tonbridge, TN9 1BR, Freephone 0800 279 0357 or email ubmidpa@ubm.com. View our full privacy policy at




















1 Readers' comment